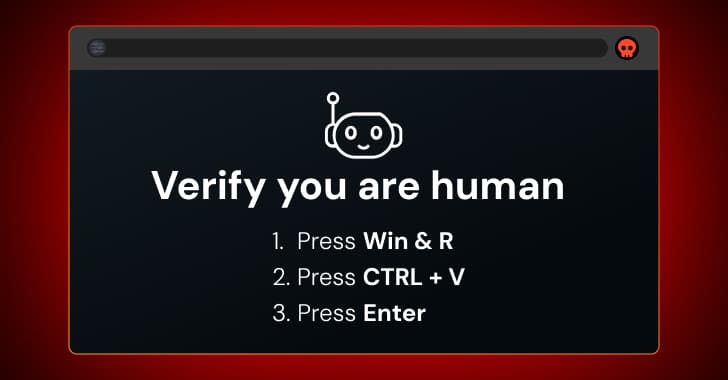
ClickFix attacks require the user to resolve a challenge or issue within the browser. By copying malicious code from the page clipboard and executing it locally, they deceive users into executing malicious commands on their device. The Interlock ransomware group and other well-known threat actors, such as state-sponsored APTs, are known to frequently use ClickFix.
ClickFix-style TTPs have been connected to several recent public data breaches, including the Texas Tech University Health Sciences Centers, DaVita, Kettering Health, and the City of St. Paul, Minnesota. Push Security researchers discovered that SEO poisoning and malvertising through Google Search was the most common delivery vector.
EDR can and should intercept the attack at several stages. Context determines whether an action is blocked in real time and the level of detection that is raised. Because the code is copied inside the browser sandbox, this action cannot be detected by standard security tools and reported as potentially harmful.
This implies that after the user has tried to execute the malicious code, the endpoint is the final and only chance for organizations to stop ClickFix. There's a good chance that your EDR coverage has gaps if your company permits contractors and employees to use unmanaged BYOD devices. To identify and address vulnerabilities in all of the apps that your staff members use, use Push.
Ghost logins, SSO coverage gaps, MFA gaps, weak passwords, dangerous OAuth integrations, and more are some examples of these. See our most recent product overview or schedule a live demo with a member of our team to find out more about Push. Return to Mail Online.
Returning to the page from which you arrived. To access the Push live demo page and product overview, click this link. An introduction to Push, a product demonstration, and a Q&A session with a Push developer are all included in the product overview.

.webp%3Fw%3D696%26resize%3D696%2C0%26ssl%3D1&w=3840&q=75)

.webp&w=3840&q=75)



%2520(1).webp&w=3840&q=75)
%2520(1).webp&w=3840&q=75)


