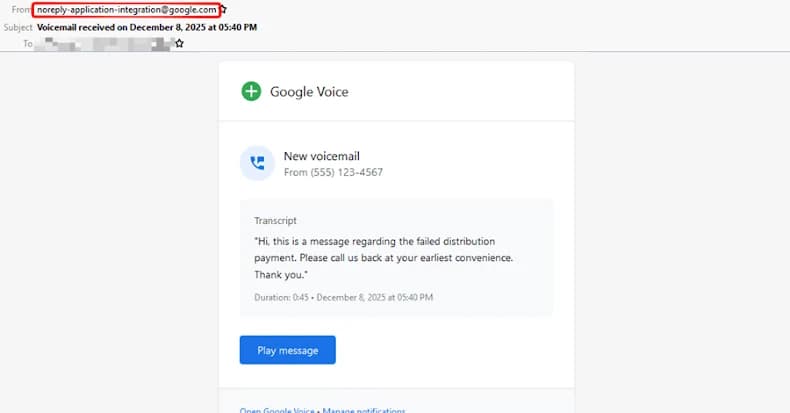
During a 14-day period in December 2025, attackers were seen sending 9,394 phishing emails to about 3,200 customers.
The misuse of Application Integration's "Send Email" task, which enables users to send personalized email notifications, is at the core of the campaign.
Google has blocked phishing attempts that exploit Google Cloud Application Integration's email notification feature, and the company is taking additional measures to stop future abuse of the feature.
When an email recipient clicks on a link hosted on storage.cloud.google[.]com, another reliable Google Cloud service, the attack chain—a multi-stage redirection flow—begins.
The user is then redirected to content served from googleusercontent[].com by the link, which presents them with a phony CAPTCHA or image-based verification that serves as a barrier by preventing security tools and automated scanners from examining the attack infrastructure.
After the validation process is finished, the user is directed to a phony Microsoft login page hosted on a non-Microsoft domain, where any credentials entered by the victims are eventually stolen.
While other industry verticals like media, education, healthcare, energy, government, travel, and transportation have also been singled out, the campaign has mainly targeted the manufacturing, technology, financial, professional services, and retail sectors.
The fact that these emails can be configured to be sent to any arbitrary email addresses demonstrates the threat actor's ability to misuse a legitimate automation capability.