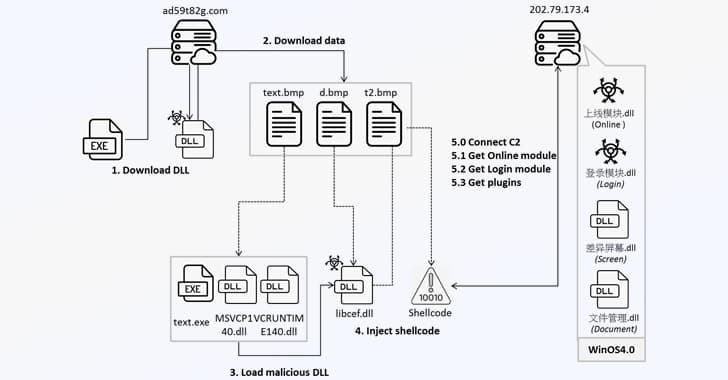
In June, Trend Micro and the KnownSec 404 Team published campaigns that distributed Winos
4.0.
The activity cluster is being monitored by cybersecurity firms under the names Silver Fox and Void Arachne. Chinese-speaking users have been the target of these attacks, which use social media, messaging apps like Telegram, and black hat Search Engine Optimization (SEO) techniques to spread the malware. The results coincide with the discovery by the AhnLab Security Intelligence Center (ASEC) of a campaign that uses phony websites that imitate gambling-related games in order to install WrnRAT malware.
"The threat actor appears to be motivated by financial gain and targets users of gambling games to capture screenshots," ASEC stated. In a blog post regarding the results of the threat cluster, Fortinet stated, "Threat campaigns leverage game-related applications to lure a victim to download and execute the malware without caution and successfully deploy deep control of the system." The company stated that "users should avoid downloading installers from illegal and suspicious sources," that the threat actor "may be targeting educational organizations," and that "illegal game users may incur additional financial losses" as a result of playing illegal games. "Winos is a powerful framework, similar to Cobalt Strike and Sliver, that can support multiple functions and easily control compromised systems," the cybersecurity firm wrote on its blog.
Schools and other educational institutions may be the target of the threat actor, who is thought to be based in China.